SSH authentication in SFTP SSH key base authentication is an access credential authentication using SSH protocol. It’s similar to username/password based authentication but here the SSH key is used instead of password. Now it become a norm to use SSH authentication in SFTP.
There are different ways to connect to your application remotely, some more secure than others. Two secure methods which we like to use ourselves are Secure Shell (SSH), and Secure File Transfer Protocol (SFTP). Both methods are supported over all our server plans include SSH and SFTP access.
- Jun 05, 2020 Public-key authentication allows the IBM i ssh, sftp, and scp clients to gain access to remote hosts without having to provide a password. The sftp and scp clients on the IBM i require Public-key authentication to gain access to ssh servers. Password authentication is not allowed with these two clients.
- To rename a key, click the key in the list, and then click Rename, or press F2. The server will verify that the name is unique and prompt you to change it if it is not. Click Close to close the SSH Key Manager. Click OK to close the SFTP Settings dialog box.
Video Tutorial — How to Connect via SSH on Windows
Video Tutorial — How to Connect via SFTP on Windows
What is SSH?
Secure Shell provides strong authentication and encrypted data communications between two computers or servers connecting over an open network such as the internet. This means that any device in the middle is unable to decipher the communication because only your end device/server is able to decrypt the information exchange.
TipYou can also run additional tools such as Composer, Git, WP-CLI for WordPress, and database queries using SSH.
What is SFTP?
SFTP stands for Secure File Transfer Protocol (also known as SSH File Transfer Protocol). It is a file transfer protocol such as FTP yet operates over a secure network protocol like SSH. We highly recommend using SFTP for file transferring because:
- It adds a layer of security.
- Transferred data is encrypted, so it is not sent in clear text.
How to Connect to Your Application Using SSH/SFTP
Prerequisites
To connect to your server or application using SSH, you will need the following:
- Master username or Application username.
- Password
- Public IP address (also known as Server IP)
We will help you locate this information on your Cloudways Platform in the next steps. Please note that the Master user has SSH access enabled by default; however, you need to manually enable SSH access for the application user(s).
SSH/SFTP — Accessing the Credentials
There are two types of credentials (Master credentials and Application credentials) on the Cloudways Platform that you can use to connect to your application. Usually, team members are provided with application credentials by the website owner. So, which credentials will you be using?
Important- If you are using Microsoft Windows you will either need to enable WLS (Windows Linux Subsystem) or else use a free third-party tool such as PuTTY . Alternatively, you can also use the built-in SSH Terminal of Cloudways Platform.
- You need an SFTP client to connect to your server remotely. In this demonstration, we are using a free third-party tool called FileZilla , which is available on Windows and macOS, but you can also use any other client. Please make sure to download such tools only from their official website to always get the latest available version.
Using Master Credentials
Log in to your Cloudways Platform using your email address and password.
- From the top menu bar, open Servers.
- Then, choose the server you wish to connect.
- Under Server Management, you can find your Public IP address, username, and password. Be sure to take note of it.
Click on credentials to copy it on the clipboard.
Using Application Credentials
Log in to your Cloudways Platform using your email address and password.
- From the top menu bar, open Servers.
- Then, choose your server where your desired application is deployed to view application credentials.
- Next, click www.
- Choose your desired application’s name.
- Under Application Credentials, you can find your Public IP address, application username, and password. Be sure to take note of it.
- Click on credentials to copy it on the clipboard.
- If there are no credentials, then you can create application credentials.
Below, you will find information about initiating connections using SSH and SFTP separately.
SSH (Microsoft Windows) — Initiating Connection
- Launch PuTTY client and enter your Host name (Server Public IP address).
- Input Port 22, which is also the standard TCP port for SSH.
- Click Open.
- You may see an RSA2 key prompt if this is your first time connecting to the server. Click Yes to make this a trusted host for future connections.
SSH (Microsoft Windows) — Logging in to Server
- Here, you need to input your master or application username, which you previously noted.
- To paste the copied item in the terminal, tap right-click once.
- The terminal screen will only work with arrow keys for navigation, not with a mouse.
- Next, input your password. Please note that no character will appear as you type the password due to security reasons.
- You are now connected to your server via SSH. Now, you can run commands such as ls to list and navigate your files and directories.
If you are using the Master Credentials, you will need to browse to your target application folder. If you are using the Application Credentials, you will land directly in the respective application folder.
SSH (Linux/macOS) — Logging in to Server
We won’t require any external SSH client for Linux/macOS, although you are free to do so if you already have some preferred 3rd party application. In this example, we are using Linux (Ubuntu).
- Open your terminal and execute the following command. Username refers to a master username or application username, and the hostname is your Server Public IP address. By default, the SSH connection is initiated using port 22.
Example: ssh master_ojnokgldl@192.168.0.1
Note: you can also point your SSH client to which private key should be used by using the -i identity switch as follows:
Tip- The terminal screen will only work with arrow keys for navigation, not with a mouse.
- You may see an RSA key prompt if this is your first time connecting to the server. Type yes to make this a trusted host for future connections.
- Next, input your password. Please note that your password will not become visible due to security reasons.
- You are now connected to your server via SSH. Now, you can run commands such as ls to list and navigate your files and directories.
- If you are using the Master Credentials, you will need to browse to your target application folder. If you are using the Application Credentials, you will land directly in the respective application folder.
- Please note that SSH is a potent tool, and advanced users use it. Executing wrong instructions may break your website and delete the critical files; therefore, we recommend using it with extra care and always take a backup of the application you are working on or take a whole server backup always to restore if needed.
SFTP — Initiating Connection
- Launch FileZilla client and enter sftp://server-ip-address in Host. By writing sftp:// , you are ensuring that the SFTP connection is formed.
- You need to input your master or application username, which you previously noted.
- Next, input your password.
- Set Port 22.
- Finally, click QuickConnect.
- You are now connected to your server via SFTP. Now, you can drag and drop files and folders between your personal computer and your server.
- If you are using the Master Credentials, you will need to browse to your target application folder. If you are using the Application Credentials, you will land directly in the respective application folder.
- If you face any permission-related issues, then you can also reset your file and folder permissions.
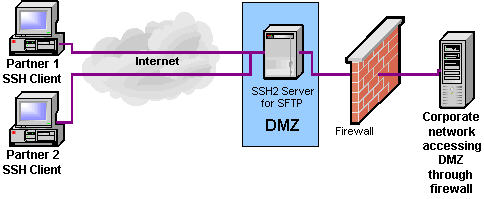
In every SSH/SFTP connection there are four keys (or two key-pairs) involved. This article explains a difference between them and what keys an SFTP client user needs to care about.
The SSH employs a public key cryptography. A public-key cryptography, also known as asymmetric cryptography, is a class of cryptographic algorithms which requires two separate keys, one of which is secret (or private) and one of which is public.1 Together they are known as a key-pair. In SSH, the public key cryptography is used in both directions (client to server and server to client), so two key pairs are used. One key pair is known as a host (server) key, the other as a user (client) key.
Sftp With Ssh Key Filezilla
A user private key is key that is kept secret by the SSH user on his/her client machine. The user must never reveal the private key to anyone, including the server (server administrator), not to compromise his/her identity.
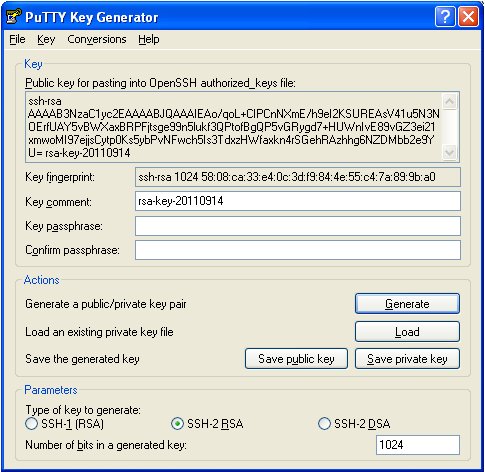
To protect the private key, it should be generated locally on a user’s machine (e.g. using PuTTYgen) and stored encrypted by a passphrase. The passphrase should be long enough (that’s why it’s called passphrase, not password) to withstand a brute-force attack for a reasonably long time, in case an attacker obtains the private key file.
Different file formats are used to store private keys. WinSCP supports PuTTY format, with .ppk extension.
A user public key is a counterpart to user private key. They are generated at the same time. The user public key can be safely revealed to anyone, without compromising user identity.

Sftp Login With Ssh Key
To allow authorization of the user on a server, the user public key is registered on the server. In the most widespread SSH server implementation, the OpenSSH, file ~/.ssh/authorized_keys is used for that.
Learn more about public key authentication in general and how to setup authentication with public keys.
Advertisement
A host private key is generated when the SSH server is set up. It is safely stored in a location that should be accessible by a server administrator only. The user connecting to the SSH server does not need to care about host private key in general.
A host public key is a counterpart to host private key. They are generated at the same time. The host public key can be safely revealed to anyone, without compromising host identity.
Sftp With Ssh Key Linux
To allow authorizing the host to the user, the user should be provided with host public key in advance, before connecting. The client application typically prompts the user with host public key on the first connection to allow the user to verify/authorize the key. The host public key is then saved and verified automatically on further connections. The client application warns the user, if the host key changes.
Ssh Key Setup
- The text is partially copied from Wikipedia article on Public-key cryptography. The text is licensed under GNU Free Documentation License.Back
